Business Information Systems Security: A Complete Guide for Modern Enterprises

Look, let’s just get real here. Data’s flying everywhere these days, isn’t it? And danger, well, it’s always lurking. So, keeping your company’s most precious stuff safe? That’s not just a sensible move; it’s a do-or-die situation. Truly effective business information systems security isn’t just for the IT folks anymore. Nope. It’s the absolute bedrock your business relies on. It makes sure you keep the lights on, keep customers happy, and honestly, just keep going. We’re talking about making sure all your digital bits and bobs are locked down tight. Keeping things running without a hitch. And earning everyone’s confidence. Yeah, it’s a huge deal.
Understanding Business Information Systems Security
So, what exactly is this all about? Well, it’s not just about slapping some antivirus on your machines, you know. Far from it. This is a complete picture. A smart mix of rules, ways of doing things, and actual tech. All designed to guard your organisation’s data against all sorts of dodgy stuff. Stuff like folks getting in who shouldn’t, someone using things wrongly, or telling secrets. Basically, anything that could muck up your important bits of info.
And it isn’t a half-baked job, either. We’re talking about locking down every single part of your info system. The physical stuff, the programs, the actual numbers and words, your connections. Most important? The people who touch all of it. Our main aim? It’s really straightforward, honestly: keep private business info private. Make sure it’s accurate and complete. And guarantee it’s there when you or authorized staff need it. Right then. That’s the long and short of it.

Why Business Information Systems Security is Crucial for Modern Enterprises
So, why’s this such a big deal now, eh? Well, the nasty bits lurking online aren’t just popping up more often; they’re getting really clever. Seriously. A strong BIS security setup isn’t just a neat extra for businesses nowadays. Not at all. It’s an absolute must-have. Just think what happens if someone gets in: big money lost, your good name dragged through the mud, maybe even lawsuits from the powers-that-be. And everything grinds to a halt. A proper mess, that.
And we reckon looking after customer info, your special ideas, and all those company secrets isn’t just good manners. It makes darn sure you can carry on ticking over, come what may. Keeps you ahead of the pack. Full stop. No two ways about it. That’s why we don’t just tack it on at the end.

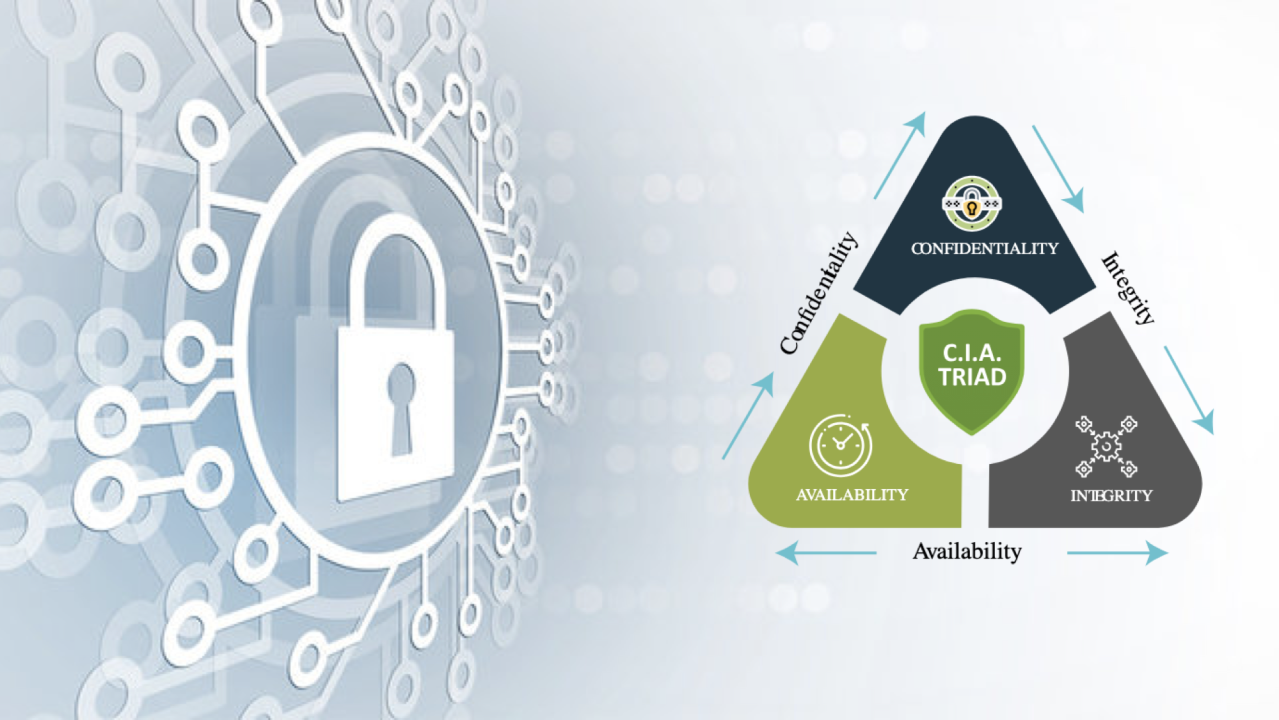
The Pillars? We Call Them the CIA Triad.
Every sturdy home needs a good base, doesn’t it? For proper business information systems security, that base stands on three main supports. We call them the CIA triad, and they’re pretty well-known: Confidentiality, Integrity, and Availability. These aren’t just fancy terms; they’re what you have to do.
Confidentiality? That means only the right people ever peek at your private info. Nobody else gets a look-in. Simple. Integrity, on the flip side, makes sure your data stays spot-on, whole, and completely un-messed-with. No monkey business. And Availability? That’s about making sure your systems and all your stuff are there, waiting, for the folks who should use them. Right when they need ’em. No stoppages means you’re open for business.
Implementing Robust Business Information Systems Security Strategies
You can’t just cross your fingers and hope for security; you’ve got to put in the work. We’ve learned that really getting business information systems security up to scratch means layering things, just like an onion. One protection won’t cut it. We’re talking about putting in place stuff like really good firewalls, clever systems to spot intruders, and tough encryption everywhere.
But the tech side? That’s only half the story. You also need to go digging for weak spots. And that’s where regular security check-ups, deep dives into vulnerabilities, and those “pretend you’re a hacker” tests come in handy. They’re absolutely essential for finding and sorting out issues before they turn into a proper catastrophe. Oh, and don’t forget the people! Strict controls on who gets in where, ongoing training so staff know the risks, and clear plans for when things go wrong are all big parts of a tough security stand. Can’t afford to skip any of that.

What Keeps Us Up at Night: Common Threats and Challenges
Look, the folks trying to cause trouble? They’re not just twiddling their thumbs, are they? Businesses today are always getting hit with loads of nasty stuff. Just picture ransomware attacks – that’s a truly scary thought – or those sly phishing emails trying to trick your staff. And people on the inside? Yeah, they can be a real problem too, causing untold damage. Plus, new, tricky bad software always shows up. It’s a never-ending scrap.
But it’s not just the direct attacks. We also struggle with how fast tech moves and how complicated IT setups get. And let’s not pretend we don’t feel the pinch from the serious lack of good cybersecurity experts. Handling the risks from other companies you work with, and staying on top of all the shifting rules for protecting data? Those are some hefty bumps in the road too. It’s a proper juggling act, no doubt about it.

Final Thoughts on Safeguarding Your Digital Future
My two cents? Putting business information systems security first isn’t just a suggestion; it’s an absolute must for any business wanting to really do well, not just get by, in today’s tech-heavy times. By really getting a handle on the dangers out there, by always putting proper plans in place, and by making sure everyone in your company thinks about security, you do more than just guard bits of info. You look after your prized possessions. You make sure things keep running without a hitch. And you defend your good name against all the changing online dangers. It’s definitely worth doing right.

